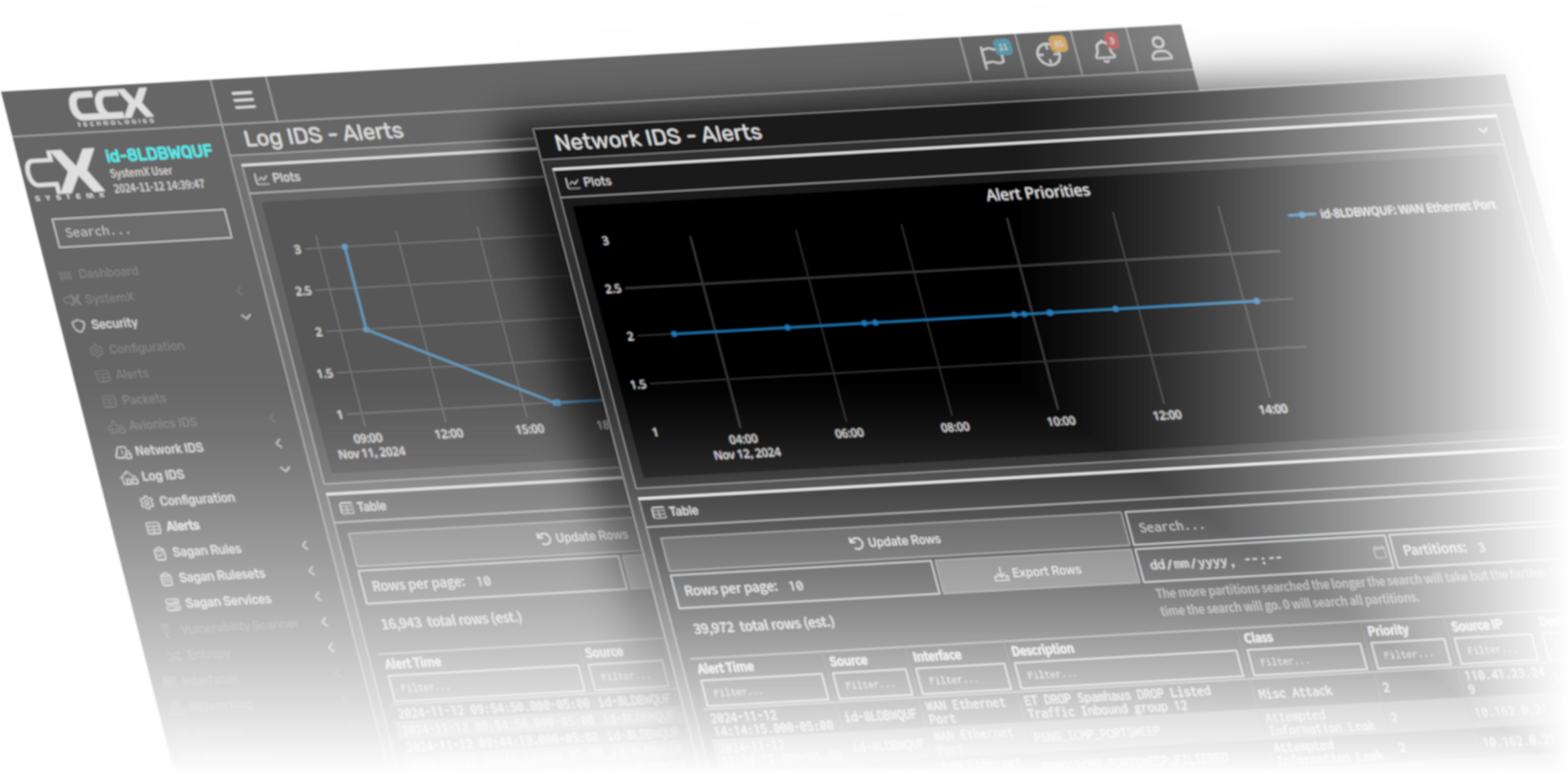
SystemX provides integrated Network and Logs Intrusion Detection Systems that can be individually managed on the edge of the network, or centrally managed from a SystemX Server.
The Network IDS can be used to monitor traffic on a specific interface or LAN and the Logs IDS can be used to monitor SystemX logs, or logs provided by external equipment and software.
Network IDS
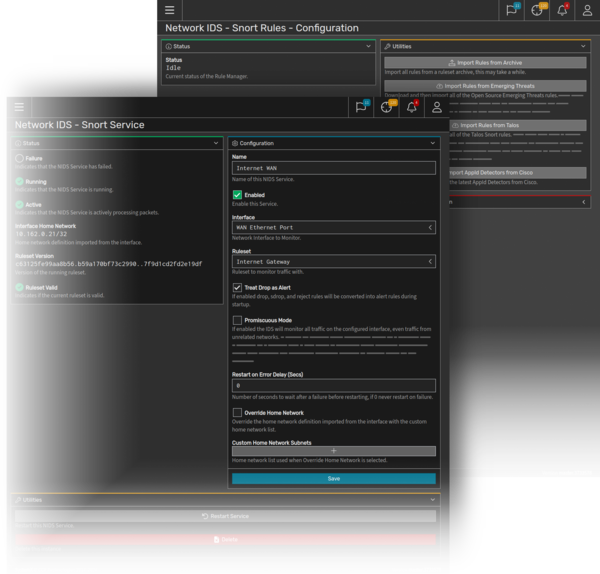
SystemX’s Network Intrusion Detection System (NIDS) uses the power of Snort to monitor a network and detect potential threats. Once a Snort service is active, traffic is continuously analyzed against a ruleset and will generate an alert if a rule is triggered.
Snort rules can be loaded onto a system via an archive file, or imported directly from the most up-to-date Talos or Emerging Threats sources.
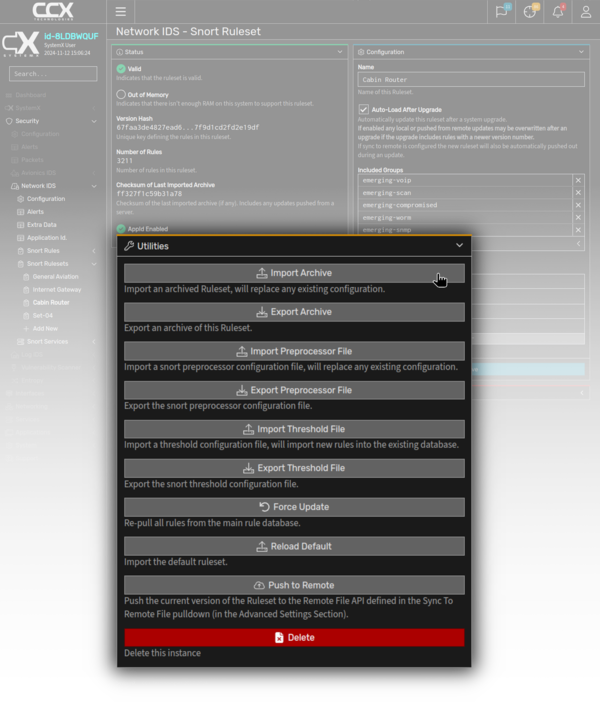
Ruleset Management
Once imported, all rules are stored in a local database and can then be grouped into rulesets. Each ruleset is then associated with its own Snort service.
Rules can be managed centrally using a SystemX Server and pushed out to an entire fleet of managed systems.
Alerts
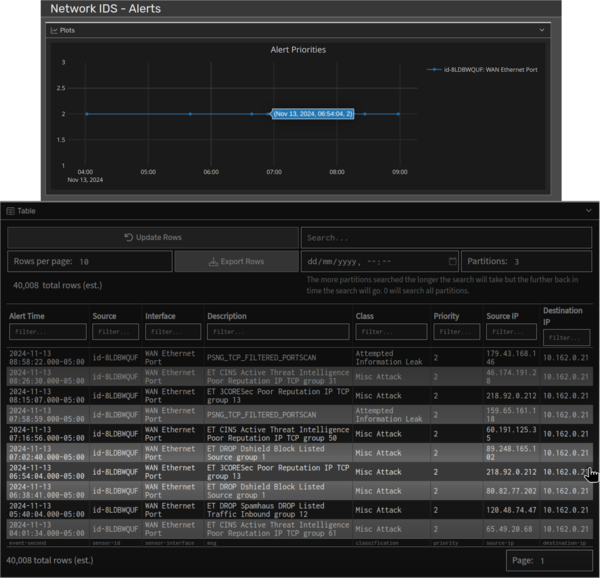
All alerts generated by a running snort service will be logged in the alerts database and can be viewed by a system administrator in real-time, or downloaded from the system after a flight.
Alerts can be pushed out to a SystemX Server for centralized alert monitoring in a Security Operations Centre, and even forwarded to third-party SIEM (Security Information and Event Management) software for cross-correlation with additional information systems.
Each alert will include important details of the event such as the source and destination IP, and the type of threat identified. For example, an attempted information leak caused by a local port scan.
Logs IDS
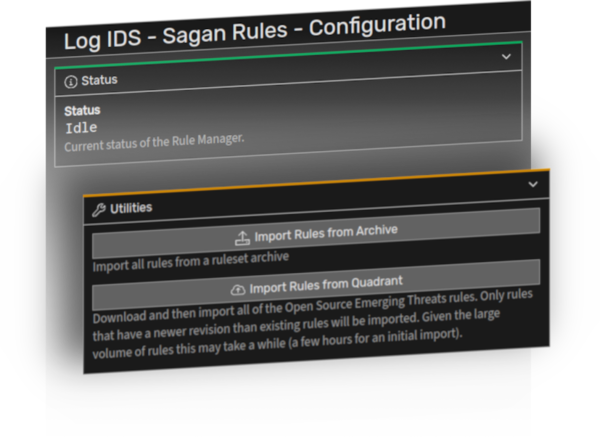
SystemX’s Logs IDS provides real-time analysis of system logs using regular expression based rules against log text. Rules are loaded onto a system via an archive file or downloaded from the most up-to-date source via Quadrant. Default rules are included with SystemX as part of the base installation.
Local logs generated by SystemX can be monitored, and logs from other equipment can be forwarded to SystemX using the Syslog Protocol.
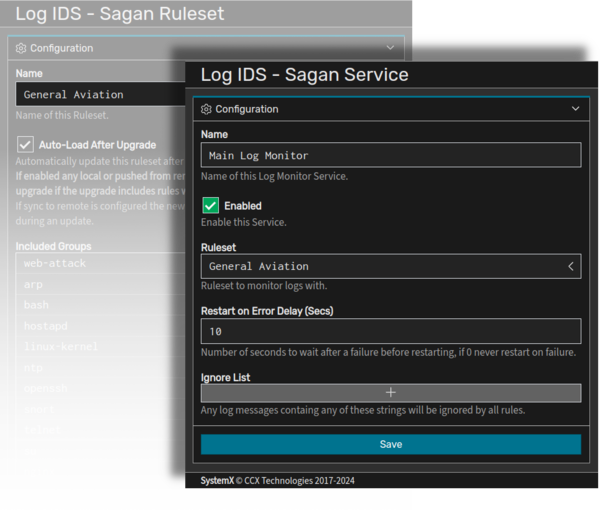
Rules are then grouped by function into a ruleset and associated with a Sagan service which monitors ingested logs and raises alerts based on text matching. Once running, the Sagan service will generate alerts when a rule is triggered by matching log activity.
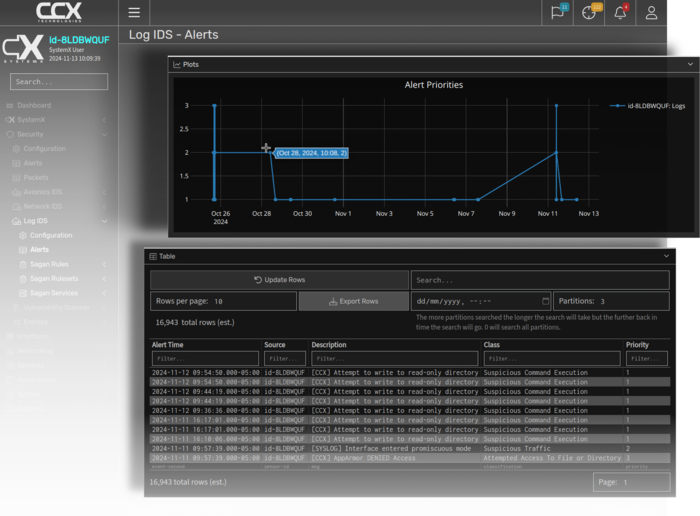
Alerts generated by a Sagan service will be logged in real-time to the alerts database where they can be viewed by security professionals or exported for analysis on the ground. Default rulesets created by CCX Technologies are already used to identify important system events or attempts to access restricted directories.
Alerts can be pushed out to a SystemX Server for centralized alert monitoring in a Security Operations Centre, and even forwarded to third-party SIEM (Security Information and Event Management) software for cross-correlation with additional information systems.
Each alert will include important details of the event such as the log text that triggered the alert, time-stamps, and source equipment labels.