CCX Technologies' SystemX Operating System includes a complete set of Intrusion Detection Systems that provide unprecedented visibility into Operational Networks.
Traffic can be monitored on traditional Ethernet and WiFi IP-based networks; on data-bus networks like MIL-1553, CAN Bus, and ARINC-429; and from plain-text logs — all using the same hardware, software, and infrastructure.
All rules and algorithms are transparent, deterministic, and user configurable. Development Kits and development environments are available to support rule and algorithm development. Generated alerts and data can be collected, viewed, and exported to any external system.
CCX Technologies provides rule and algorithm development services and can provide support for development by third-parties. For security restricted systems it is possible for a third-party to develop and use algorithms and rules without exposing them to CCX Technologies.
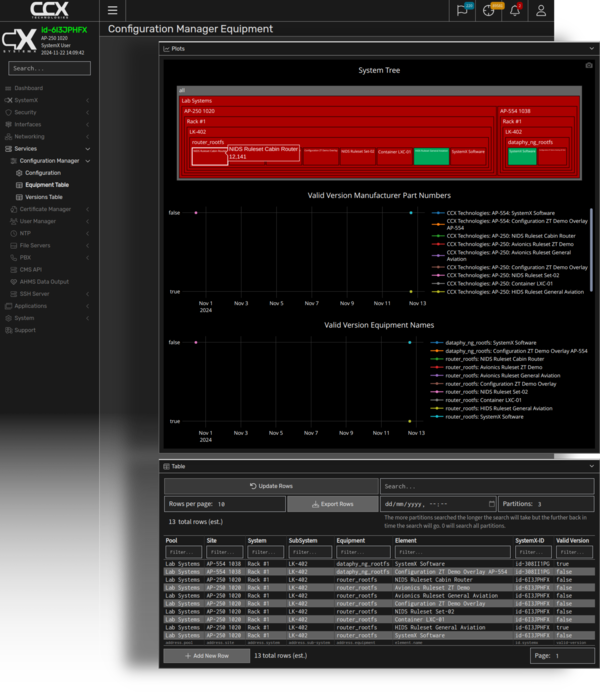
Fleet Management
SystemX provides all of the tools required to manage a fleet of intrusion detection systems. Alerts and captured data are forwarded to a central server, either in real-time over existing connectivity systems, or post-mission using secure maintenance laptops or other maintenance connectivity systems.
New rulesets and algorithms can be pushed out to a fleet of systems using the same infrastructure used to collect alerts and data.
A SystemX ground server can be used to analyze collected alerts and data. Alerts and other system state data can also be forward to external SIEM systems.
Captured traffic is stored in encrypted local databases on SystemX equipment, allowing for detailed forensics investigations for any generated alerts.
Data-Bus IDS
Using the CCX Technologies Falcon IDS within the SystemX ecosystem it is possible to collect, decode, and monitor data-bus data from any supported data-bus, including MIL-1553, ARINC-429, and CAN Bus.
Data can be collected using any CCX Technologies DataPHY or Secure Router, or from third-party data collection systems.
The IDS itself can run on any CCX Technologies Secure Router, or as a virtual machine on other application hosting systems.
Algorithms can be created for a multitude of scenarios. For example, identifying an anomalous rate of change in a vehicle’s speed due to a GPS spoofing attack, or detecting the injection of malicious data into a MIL-1553 data bus.
SystemX includes a set of default algorithms which can be configured with specific rules to identify many common data-bus anomalies.
A built-in editor and algorithm development environment can be used to write and modify algorithms on a development system, and a stand-alone falcon simulator can be extracted from a system for offline development of complex algorithms and decoding software.
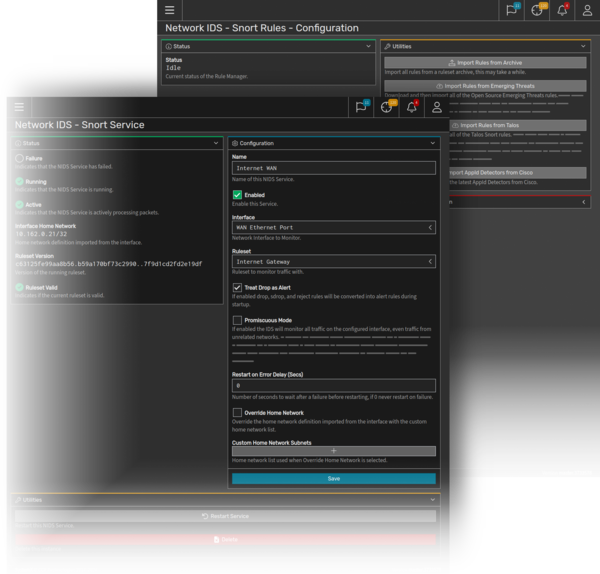
Network IDS
SystemX’s Network Intrusion Detection System (NIDS) uses the power of the industry standard Snort IDS to monitor IP traffic on a network and detect potential threats.
SystemX includes a set of default rules and rulesets. New Snort rules can be created on the system, or externally sourced.
Logs IDS
SystemX’s Logs IDS provides real-time analysis of system logs using regular expression based rules. Plain text logs from a local SystemX instance can be analyzed and logs from third-party equipment can be ingested and analyzed.
SystemX includes a set of default rules and rulesets and new rules can be created on the system, or externally sourced.